In a previous blog post, we introduced how to leverage BloodHound to visualize attack paths in Active Directory. This post will follow up on those ideas, presenting the importance of implementing a tiered administrative strategy in your domain.
A tiered strategy is nothing new – Microsoft originally recommended this over 10 years ago with guidance for mitigating “Pass-the-Hash” (PtH) Attacks. The general idea is to classify objects and assets within Active Directory based on three tiers.
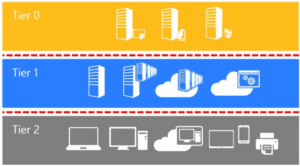
Tier 0
Tier 0 includes all assets that are deemed as critical in the environment, such as Domain Controllers, Active Directory Certificate Servers, Active Directory Federation Services, etc. These are essentially the keys to the kingdom – if one of these assets is compromised, it can be assumed the entire domain is as well.
Tier 1
This tier covers member servers in the environment. For example, any file share servers, web servers, and SQL servers within your environment.
Tier 2
The final tier includes all workstations and laptops that a typical end user would access for day-to-day operations.
Source: Microsoft
With assets properly classified to their respective tier, relevant accounts and permissions can be created. Desktop support teams should have a secondary workstation admin tier account that does not have special privileges on the domain or servers. Similarly, a SQL administrator can have a dedicated server tier admin account and could be denied access to other tiers and so on.
Principle of Least Privilege Reality
Simply stated, the DenSecure team has rarely seen this strategy formally adopted. Instead, a common approach is to only separate low-privileged users and administrators.
Below, is an example we have seen in many production environments:
- Users with authorized administrative rights are provided a daily driver account with no special privileges to browse the Internet, view e-mail, etc.
- An elevated account is created and typically denoted with “-adm” or “sa.” The account is granted membership to default security groups, often part of the built-in Domain Admins group.
On paper, this appears to meet the requirements of implementing the principle of least privilege. Standard users do not have admin rights in the environment, and elevation to a secondary account is needed to install software, make group policies, and implement other significant changes to the domain.
However, what is hidden to defenders is the fact that active logon sessions will be left throughout the environment on workstations, servers, and domain controllers. This is never revealed in a vulnerability scan and unfortunately missed in various penetration tests.
A “session” occurs whenever an account is logged onto a system interactively. These sessions persist for quite some time, can be enumerated by any standard user, and are targeted by adversaries for impersonation and credential theft.
The cost and effort of compromising a workstation with an administrative logon session is much lower compared to compromising a domain controller. The SpecterOps team have created a video to explain user session enumeration and the potential for abuse using BloodHound here.
Per BloodHound:
“When a user has a session on the computer, you may be able to obtain credentials for the user via credential dumping or token impersonation. You must be able to move laterally to the computer, have administrative access on the computer, and the user must have a non-network logon session on the computer.”
Although Microsoft has recently updated guidance on hardening on-premises Active Directory, a tiered administrative strategy is still consistently recommended. Proper implementations ensure that even after a successful compromise, an actor is limited to only interacting with systems in the same tier.
For instance, during a penetration test in which we successfully compromise a workstation, regardless of if we elevate our permissions, we would in theory only be able to have access to a tier 2 admin account instead of an account with tier 0 privileges. This roadblock provides defenders with more time to identify malicious activity and forces us to enhance our tradecraft and deploy more sophisticated attacks.
Source: Microsoft
If you want to have a conversation about common Active Directory attacks, hardening strategies, or any other security issue, we’re here to help – reach out to DenSecure today!





