Throughout our penetration testing engagements, we find that we can gain an initial foothold in the domain or gain user credentials easier. Why? The following underlying protocols are fallback protocols for when domain naming service (DNS) ultimately fails. With most of our clients, we hear that “we fixed these protocols,” or that “these protocols have no risk associated with them,” but when their DNS server fails, these protocols become the fallback and our attacker device command line lights up like a Christmas tree. Throughout this blog, we show how an attacker would best utilize these protocols, what can happen if these protocols are in use, and how to best remediate them.
What Are NetBIOS, LLMNR & mDNS?
NetBIOS-NS stands for network basic input/output system naming service. This protocol runs on UDP/TCP port 137, 138, and 139, mostly on Windows hosts running Server Message Block (SMB) and the Unix-based version, Samba. This protocol asks the receiving machine to disclose and return its current set of NetBIOS names.
Figure 1: NetBIOS-NS Poisoning
LLMNR stands for Link-Local Multicast Name Resolution. This protocol runs on UDP port 5355, mostly to perform name resolution for hosts on the same local link. It mostly includes all Windows hosts and has been implemented in Linux for the systemd-resolved service.
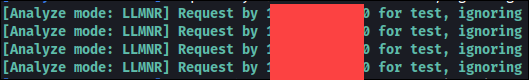
Figure 2: LLMNR Poisoning
mDNS stands for Multicast DNS. This protocol runs on UDP port 5353 and was originally made by Apple to help the AirPlay2-based services perform seamless setup via the Bonjour service. Now, it is found primarily in networks with mostly Windows and internet of things (IoT) devices. This protocol performs local network name and service discovery without the need for central name resolution.

Figure 3: mDNS Poisoning
These protocols are a penetration tester’s best friend. All these protocols are used to resolve host names on local networks. When a local network needs to resolve “google.com” to its IP address of “x.x.x.x,” computers or internet of things (IoT) devices follow a hierarchical approach when querying the target resource:
- Check to confirm whether the request is for the local machine name.
- Check the local cache of recently successfully resolved names.
- Search for a local host file, which is a list of IP addresses and names stored on the local computer. Depending on the device, this file might already be loaded into the local cache.
- Query a DNS server if one is configured.
- If NetBIOS is enabled, attempt NetBIOS name resolution via broadcasting NetBIOS-NS queries to the local subnet if the name is not in the local NetBIOS cache. This step might use a Windows Internet Name Server (WINS) server if configured and the LAN manager hosts (LMHOSTS) file.
- If LLMNR is enabled, broadcast LLMNR queries across the local subnet network to ask its peers for resolution.
- If mDNS is enabled, the appropriate client sends a multicast into the network while asking which network participant matches the hostname.
In short, if the DNS fails at any point to resolve the name of the hosts during the process above, LLMNR, NetBIOS, and mDNS take over to keep everything in order on the local network.
The Attack
The inherent problem with these protocols is the trust the victim computer assumes with other devices in its segment of the network. If a computer cannot properly identify the resource it is looking for among the first four steps, the different local naming resolution protocols come into play. The best example of this is when a user mistypes the name of a resource, requests a resource that is no longer available, or a user begins to type in the Windows start menu. For example, typing \\testt\ when the \\test\ share is the correct file share. This would allow the attacker to poison the request and say “Hi, I am \\testt\, authenticate to me!”
In Summary:
-
- User incorrectly enters a hostname that gets queried on the local network.
- The domain controller responds and states that the hostname does not exist in DNS.
- The host discovery protocols, LLMNR, mDNS, and NetBIOS-NS broadcast the request.
- The attacker responds to the host discovery protocol stating that the attacker is the host being sought and that the user should authenticate to the attacker.
- The workstation sends authentication credentials to the attacker either in the form of username and password, or the user’s password encoded in NTLMv1 or NTLMv2 format.
- With these credentials, an attacker can either replay the hash to another computer and obtain a session or attempt to crack the hash offline.
- If an attacker receives a plaintext password, the attacker now has domain credentials and the same access as the user.
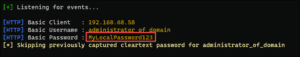
Chromium browsers (including Google Chrome, Safari, and Microsoft Edge) do use mDNS to locate printers and use Chromecast (Chrome) or AirPlay (Safari) on the internal network, which broadcasts on the accessible subnet. This is a known issue.
Mozilla Firefox has been tested and does not broadcast mDNS on the accessible subnet as it does not rely on mDNS to discover printers.
When a user requests to find a printer, as illustrated below, the Chromium browser utilizes mDNS to find that printer, and an attacker would be able to poison that request.
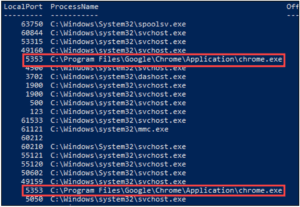
Figure 4: Chrome mDNS Discovery
Remediation Steps
These legacy protocols provide redundancy when DNS fails. An organization should investigate adopting more modern services such as DNS to ensure that compromises don’t happen.
There are several ways to mitigate such attack vectors:
- Via GPO (Group Policy Object) (LLMNR and NetBIOS-NS): this allows for remediation of both LLMNR and NetBIOS-NS but does not remediate mDNS. To remediate mDNS, a registry key needs to be added to the local Windows host (see #2 below).
- Computer Configuration > Administrative Templates > Network > DNS Client > Turn off Multicast Name Resolution > Setting “Enabled”
- Force GPUpdate “gpupdate /force”
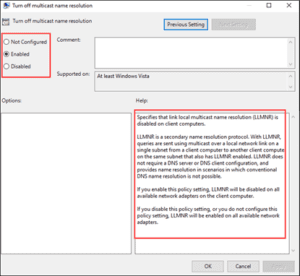
Figure 5: Multicast Name Resolution via GPO (Group Policy Object)
-
- Via Registry (LLMNR, NetBIOS-NS, and mDNS): this helps to remediate mDNS, LLMNR, and NetBIOS-NS on the local host, but if the Windows Internet Name Service (WINS) is allowing NetBIOS-NS requests, then that needs to be disabled as well (see #3 below).
- “HKLM:\SYSTEM\CurrentControlSet\Services\Dnscache\Parameters”-Name “EnableMDNS”-Value 0-Type DWord
- Via Registry (LLMNR, NetBIOS-NS, and mDNS): this helps to remediate mDNS, LLMNR, and NetBIOS-NS on the local host, but if the Windows Internet Name Service (WINS) is allowing NetBIOS-NS requests, then that needs to be disabled as well (see #3 below).
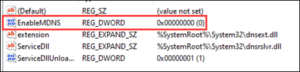
Figure 6: Disable mDNS Registry
-
-
- “HKLM: SYSTEM\CurrentControlSet\services\NetBT\Parameters\Interfaces” -Name NetbiosOptions -Value 2
-
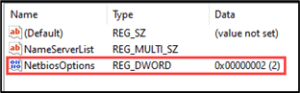
Figure 7: Disable NetBIOS-NS Registry
- Via Control Panel (NetBIOS-NS): this helps to disable NetBIOS-NS on the local Windows hosts.
- Launch Control Panel from the Start Menu
- Make sure your View by is set to Large Icons and click Network and Sharing Center > Change adapter setting
- Right-click on the connected network and select Properties
- Select Internet Protocol Version 4 (TCP/IP) and click Properties
- Click Advanced > WINS > Disable NetBIOS over TCP/IP > Ok
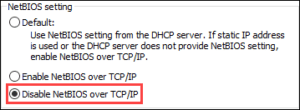
Figure 8: Disable NetBIOS-NS via Control Panel
-
- On IoT devices, Linux, and Apple devices
- Depending on the device, some need to be locked down more than others, and some services may suffer.
- For instance, the Avahi service running on Linux may need to be locked down with the Uncomplicated Firewall (UFW).
- The daemon registers local IP addresses and static services using mDNS/DNS-SD and provides two IPC APIs for local programs to make use of the mDNS record cache the avahi-daemon maintains.
- To disable the avahi-daemon:
- sudo systemctl stop avahi-daemon.service
- sudo systemctl stop avahi-dnsconfd
- On IoT devices, Linux, and Apple devices
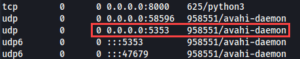
Figure 9: Avahi Daemon
-
- Apple Devices need the Bonjour service to locate other Apple Devices (i.e., AirDrop, AirPlay, etc.).
- Bonjour, also known as zero-configuration networking, enables the automatic discovery of devices and services on a local network using industry-standard IP protocols.
- MacOS relies on mDNS for services such as AirPlay and may not function properly. To disable the mDNSResponder:
- sudo launchctl unload /System/Library/LaunchDaemons/com.apple.mDNSResponder.plist
- sudo launchctl unload /System/Library/LaunchDaemons/com.apple.mDNSResponderHelper.plist

Figure 10: Open Port MacOS
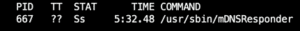
Figure 11: mDNSResponder (Bonjour)
- Printers utilize the Bonjour service or mDNS when hosts attempt to discover printers, but do not need LLMNR.
- To remediate the Bonjour service, disable it through the web console; however, this may not allow users the ability to find printers on the local network.
- Apple Devices need the Bonjour service to locate other Apple Devices (i.e., AirDrop, AirPlay, etc.).
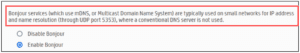
Figure 12: HP Printer Bonjour Service Sample
-
- Detecting local network protocol usages on Windows hosts
- This gives the ability to log and monitor all the protocols mentioned in this article on Windows hosts.
- Enable Windows Filtering Platform via GPO:
- Domain Policy > Computer Configuration > Policies > Windows Settings > Security Settings > Advanced Audit Policy Configuration > Audit Policies > Object Access > “Audit Filtering Platform Connection” & “Audit Filtering Platform Packet Drop”
- After the logs are enabled, the Event IDs 515_ will give a description of what is being blocked or allowed (depending on risk) including inbound and outbound network information (see Figure 14).
- Detecting local network protocol usages on Windows hosts
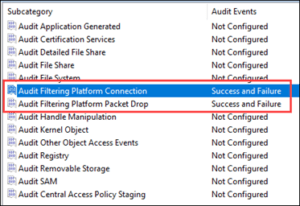
Figure 13: Auditing via GPO
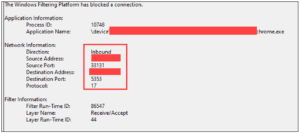
Figure 14: Event Viewer Logging
-
-
- Either block or allow (detect) mDNS, LLMNR, and NetBIOS-NS on Windows Defender Firewall.
- New rule on Windows Defender Firewall (Inbound and Outbound)
- Protocol and Ports
- UDP: 5353 (mDNS), UDP 5355 (LLMNR), UDP/TCP 137,138,139 (NetBIOS).
- Depending on risk (“Allow the connection” or “Block the connection”)
- Profile: All
- Name: Block (or Detect) Legacy Protocols
- Description: Yes
- New rule on Windows Defender Firewall (Inbound and Outbound)
- Either block or allow (detect) mDNS, LLMNR, and NetBIOS-NS on Windows Defender Firewall.
-
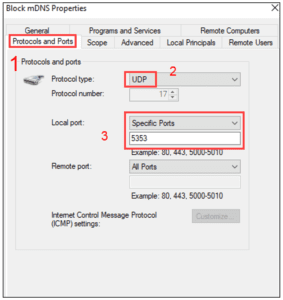
Figure 15: Windows Defender Firewall
-
-
-
- Right-click on Windows Defender Firewall with Advanced Security
- Under “(Domain/Private/Public) Profile,” click Customize
- “Log dropped packets” – “Yes”
- “Log Successful Connections” – “Yes”
-
-
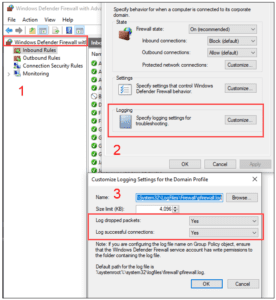
Figure 16: Windows Defender Firewall Logging
In conclusion, these legacy protocols are visible on all networks, and these protocols are actively exploited allowing for easier compromise of the network. During a 2021 data breach, these protocols assisted the Lazarus group in harvesting credentials. The group used a “credential harvesting tool named ‘Responder’ and was able to laterally move using various Windows commands.” Responder is an LLMNR, NetBIOS-NS, and mDNS poisoner. This tool “was executed from one of the victim machines that had received the spear-phishing document.” (Lazarus targets defense industry with ThreatNeedle).
These protocols are not only harmful by themselves but can be combined with other techniques to allow attackers to further compromise an organization’s network. Taking the appropriate steps to mitigate these vulnerable protocols will ensure that your organization reduces the risk of losing sensitive data, monetary value, or reputation loss. Use the above guide to help ensure that none of this happens to your organization.
Legacy Protocols Are Leaving You Exposed: How Wolf’s DenSecure Team Can Close the Gaps
Outdated name resolution protocols like NetBIOS, LLMNR, and mDNS are prime targets for attackers. Our team of advanced cybersecurity professionals, DenSecure, specialize in identifying and eliminating these hidden risks through targeted assessments and advanced penetration testing.
Partner with our team to strengthen your defenses and reduce your attack surface.