Written by: Joseph Sarkisian, OSCP, GWAPT
Ever since I got into security, I have been interested in social engineering–specifically the physical part of testing. Being paid to legally “break” into a building and gain access to sensitive areas will certainly get your adrenaline pumping.
Part of this excitement comes with all the cool “gadgets” (social engineering testing tools) I get to play with. I own a tool called a Proxmark, which is a small device that can read, store, write, and replay an RFID badge (the kind you’re likely wearing on your waist or neck right now at the office) if it gets close enough to one, roughly about 3-4 inches.

Figure 1 – Proxmark
While this is useful, it requires getting that close without arousing suspicion in order to “sniff” the badge.
Another challenge is the necessity to use the stolen badge credential after successfully storing it on the Proxmark. While the device can replay a captured badge immediately after acquiring it, it looks suspicious to hold it up to every door you need to enter on an assessment – what if you’re caught and are asked to show the badge you just entered the building with?
Yet another challenge is that even if you have the time to create a cloned physical card from the one you just sniffed, you need to plug the Proxmark into a computer and program the new card, likely requiring you to leave the site and come back later.
But what if there was a way to avoid the Proxmark completely? What if there was a solution the literal size of a postage stamp that would help me get into most buildings without arousing any suspicion at all?
Enter the ESPkey.
Figure 2 – ESPkey
This tool is meant to be wired directly in line between where the badge reader sniffs for cards as people scan their badges for entry, and the back-end logic controller that determines if the person who is attempting access should be allowed in or not – a classic “man in the middle” attack. Given that this data is hardly ever encrypted in transit, the ESPkey can sniff it and store for later use.
You may be wondering what good this does since removing a badge reader cover from the wall, wiring the device into it, then closing the cover and walking away doesn’t sound all that convenient nor stealthy, not to mention you would then have to come back later and do it all over again to extract the device and all the cards it stored.
Did I mention it has a wireless access point built-in?
The real “James Bond” aspect of the ESPkey is that once powered on, it broadcasts a wireless access point that I can connect to remotely and view all the cards that it has stored in real time. I can then choose any of the stored credentials and replay them back to the reader to open the door whenever I want. Cool, huh?
The following image shows a proximity card reader with the cover removed to view the internals and placement of the ESPkey.

Figure 3 – ESPkey Operation Flow
But what if I don’t want to go to the trouble of dressing up like a construction worker to then remove a reader from the wall and install the ESPkey, possibly damaging wires in the process of installation and removal, all while not getting caught?
Instead, what if I bought a proximity card reader that can read cards from 2 feet away, installed the ESPkey inside of it, powered it all with a 15-volt DIY battery pack, stored it inside a laptop bag, and then followed employees as they walk back and forth between the office and the sandwich place they eat lunch at every day?
Well, I did–and anyone else can–do just that. While the first two pictures are a smaller version of a reader that works from about 6 inches, it’s simply a matter of swapping out this reader for another meant for garage door installs that can scan from much further.

Figure 4 – Mobile Card Reader Internals

Figure 5 – Mobile Card Reader Complete
And here is the larger size reader that scans from 1.5-2 feet.

Figure 6 – Long Range Reader Front

Figure 7 – Long Range Reader Back

Figure 8 – Long Range Reader in Laptop Bag

Figure 9 – Would You Suspect Anything?
At this point, we have all we need for a totally mobile badge sniffing operation. The only thing left to do is pick a card, any card, to clone without the need for a computer or our Proxmark.
For $50-$100, I can buy a handheld device that can write stolen badge data to a blank RFID card in seconds.

Figure 10 – Badge Programmer
And to add icing on the cake (for about $150), I can buy a used badge printer to clone an organization’s badge design based off pictures I find of employees wearing them at work.

Figure 11 – Badge Printer
Let’s say I cloned the design of an organization’s badge, complete with my picture, and printed a few to take with me. I have been walking around the area of this organization collecting employee badges as I pass them, then head to the nearest coffee shop. I connect to the ESPkey’s wireless access point from my phone and view the collected badges.
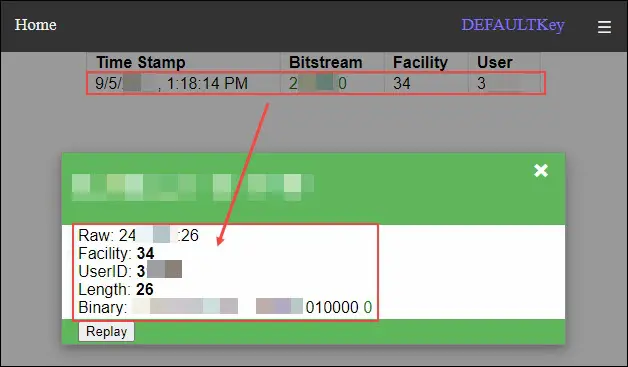
Figure 12 – ESPkey Stolen Badge Data
I pick one and then use my handheld badge programmer to input the badge user ID and other relevant information. I then write this data to the card(s) I printed at home and am now essentially the newest employee of that organization.
This may sound like cheating, and I can understand why. You may be thinking that this social engineering scenario is unlikely to happen in your organization, and while that may be true, the larger point is that this build can be purchased and assembled for well under $500 and in less than an hour of time.
What can you do about it? The same thing I would tell any of my clients: focus on the human component and remember the principles of defense in depth.
Humans are the ones responsible for installing door locks, configuring cameras and access control systems, and training their fellow employees on the risks involved with physical security.
When humans install those door locks incorrectly, don’t change the defaults on camera systems or other security controls, buy a physical access control solution that does not encrypt data or alert based on anomalies (like the same user badging in twice without badging out), holes can be poked in an organization’s security posture that could have devastating consequences.
Forget about APT29 flying a team in from Moscow to bug your executive suite at a regional bank – this is not your threat model. As sad as it is, your threat model is more likely someone entering your facilities with violence on their mind. The number one goal of your organization’s physical security procedures is not your data, not your computers, not your vault – it is the safety of the people you welcome in every day.
No single control is going to stop an attacker, which requires you to ensure every level of your physical security is hardened. If the bad guy makes it past your front door, is that it?
- Is there a security officer keeping an eye out in the lobby?
- In a managed building with lobby security, do you also have a receptionist once visitors make it upstairs?
- Are the cameras pointed in the right direction, and better yet, working?
- Are door locks and sensors properly installed to disallow simple bypass?
- Are specific areas of access restricted to only those who have a need based on job function?
- Is your cleaning crew vetted? Do they understand and agree to your security measures?
- If you have in-house security, do they watch the cameras regularly, perform rounds, or check doors for intentional shims or other irregularities?
- Are your people trained to not allow others tailgating them through a locked door? What about asking visitors for identifying information, and then escorting them until validated?
All of these measures and more create a defense in depth model for your physical security program. Remaining vigilant, regularly testing your controls, and educating your employees on the risks involved with poor security standards will help keep everyone safe and sound in the workplace.