If you’ve ever had an internal network (or “Assumed Breach”) penetration test performed by DenSecure before, you’ve likely heard of BloodHound, the tool that we use to map your Active Directory (AD) and Azure environments to help make our bad guy dirty work a whole lot more visual (read: easier).
While this tool was developed by those on the red side of testing over at Specter Ops, it simply functions as a graphical mapping tool for your AD environment. This makes it a dual-use technology in that we as testers can use it to find ways to exploit misconfigurations, while you can use it to find those same misconfigurations and remediate them before we – or the real baddies – come knocking.
This tool is quite easy to set up in your environment. Here’s what you’ll need:
- Either a Linux or Windows host (could be a virtual machine) with network access
- Either the py ingestor Python script or SharpHound executable (if you’re using Windows)
- Follow the BloodHound GUI installation directions here for Linux or here for Windows
- Follow the BloodHound data collection instructions here for SharpHound and here for BloodHound.py
A sample ingestion command from Linux using the BloodHound.py ingestor script would look like this (SharpHound has similar functionality):
![]()
- -d: the domain name for the internal environment
- -u: a valid Windows user account name
- -p: the account’s password
- -c: the collection type you want to use (see the BloodHound.py docs for more info)
Once run, you will get several JSON output files in the directory you ran the script from. Start the BloodHound GUI and you will see the window below where you can either upload the ingestion files individually, or zip them all into one folder and drag/drop them into the GUI itself:
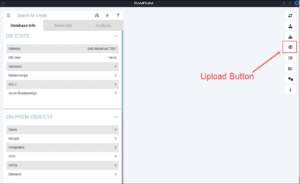
Once you have ingested your data it’s time to start hunting! First things first: mark the user with whom you ran the ingestor script as an “owned” user.
Find their account in the search window at the upper left area of the screen. Then, right click on the user node and you will see the following context menu. Click on “Mark User as Owned”:
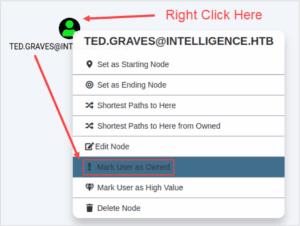
Note: This shot is part of a “Hack the Box” challenge and is not client data.
Next, within the GUI there are some predefined analysis queries you can run to catch some low-hanging fruit. Click on the “Analysis” tab and you will see the following:

We find the following queries to be most useful for quick wins:
- Find All Paths from Domain Users to High Value Targets
- Find Dangerous Privileges for Domain Users Groups
- Find Domain Admin Logons to non-Domain Controllers
- Find AS-REP Roastable Users (DontReqPreAuth)
- Shortest Paths to High Value Targets
- Shortest Path from Owned Principals (this is why you set the user as “owned” above)
If some queries come back with no data, this may mean that no issues were found, but it is always important to have a penetration test or other type of review performed to ensure the accuracy of the results. Nobody likes false negatives!
BloodHound has plenty more functionalities, but hopefully this primer helps you to start hunting Active Directory holes in your environment before the bad guys catch them. If you want to chat more about how we can help with BloodHound or any other security issue, we’re here for you!





