In a past DenSecure blog, we examined the shortcomings of many security awareness training programs. To extend the discussion, this post will dive into the technical details of a social engineering attack that targets the device code authentication flow.
Many applications and cloud services support device code authentication, and you may already be familiar with this protocol if you have set up any popular streaming services for family members, such as Netflix, Hulu, etc. Therefore, we will examine how to abuse this protocol and demonstrate how a malicious actor can compromise Microsoft 365 accounts, since “simply reporting on a click rate or credential compromise rate alone does not matter.”
 Example Authentication
Example Authentication
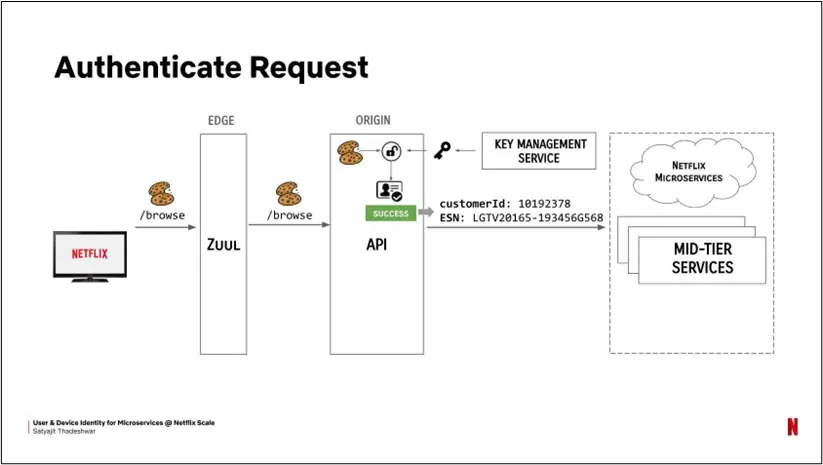
The device code authentication process assists in authenticating devices where a traditional browser or interactive session may not be possible. For example, a TV, command shell, and more can take advantage of this flow to gain access to resources, such as your most recent binge-worthy show.
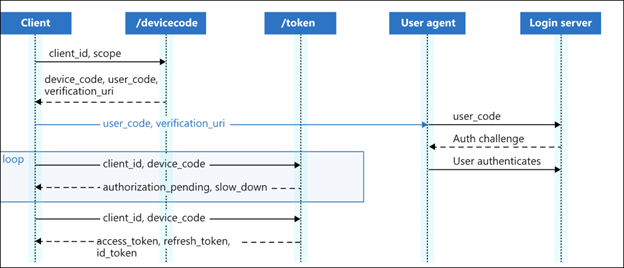
As defined in RFC8628, an attacker can perform a social engineering attack by instructing a target to register a malicious application using a device code. Below is an example of the authentication process for Netflix to authenticate a TV:
 Device Code Authentication Flow
Device Code Authentication Flow
Outside of streaming services, cloud providers have also implemented this protocol. For instance, Microsoft 365 supports this authentication flow. They stated, “The Microsoft identity platform supports the device authorization grant, which allows users to sign in to input-constrained devices such as a smart TV, IoT device, or a printer. To enable this flow, the device has the user visit a webpage in a browser on another device to sign in. Once the user signs in, the device is able to get access tokens and refresh tokens as needed.”
By default, this endpoint is accessible, and any user can complete this flow. The trick is that anyone can generate the device code and if the target victim completes the authentication flow, we receive their access/refresh tokens. The code generation is well documented and trivial to complete as seen in the following Microsoft example:
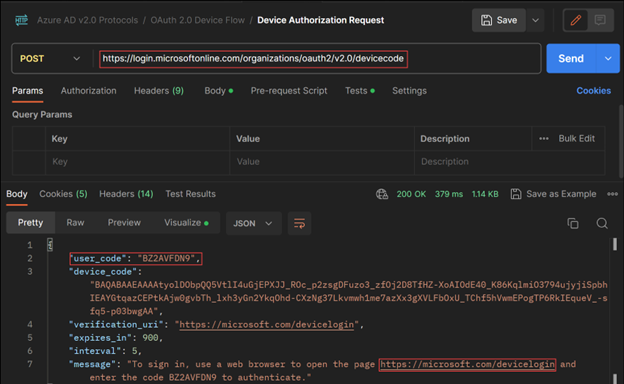
This can easily be extended and deployed in a social engineering attack as documented here.
In this attack, we are relying on Microsoft 365 entirely to create our phishing infrastructure. This attack builds trust not only with a target, but with a variety of security controls.
If you are a defender, or authorized security tester that only considers users that click a link as “failed,” it is time to reconsider security testing and awareness. Training is often built to showcase the skills of marketing, instead of actually providing valuable and actionable information for end users. Instead of just focusing on clicks (already unrealistic), users need to be trained on valid authentication flows and feel comfortable reporting abnormal requests. More on this has been detailed by TheParanoids in this article.
As always with a strong enough pre-text, the majority of users will most likely authorize an application. Do you have confidence in your users and have you tested them? For more information, please reach out to a member of our DenSecure team.