Once you have run your first threat emulation test, you’re likely to face holes in your control environment. Perhaps your preventive controls didn’t block things as you expected, or maybe the alerts were not triggered to allow your investigations to start. This blog post focuses on leveraging the D3FEND™ Matrix to identify controls that mitigate specific gaps identified in your emulation scenario.
MITRE D3FEND is funded by the National Security Agency (NSA) Cybersecurity Directorate and managed by the National Security Engineering Center (NSEC) which is operated by The MITRE Corporation. This has placed a massive amount of brainpower behind the goal of creating an inventory of defensive security techniques that is mapped to the standard adversary technique inventory, MITRE ATT&CK®.
Password spraying tactics are an excellent example of how D3FEND builds upon the intelligence you can gather form ATT&CK. A password spray attack involves the attacker enumerating likely username and password combinations and attempting each combination at any publicly available login. When looking at the technique page (T1110.003) we are presented with three mitigations and two additional detection suggestions. D3FEND™ is where we can turn for more options. At the time of writing, the D3FEND™ entry for password spraying includes a total of 18 defensive controls:
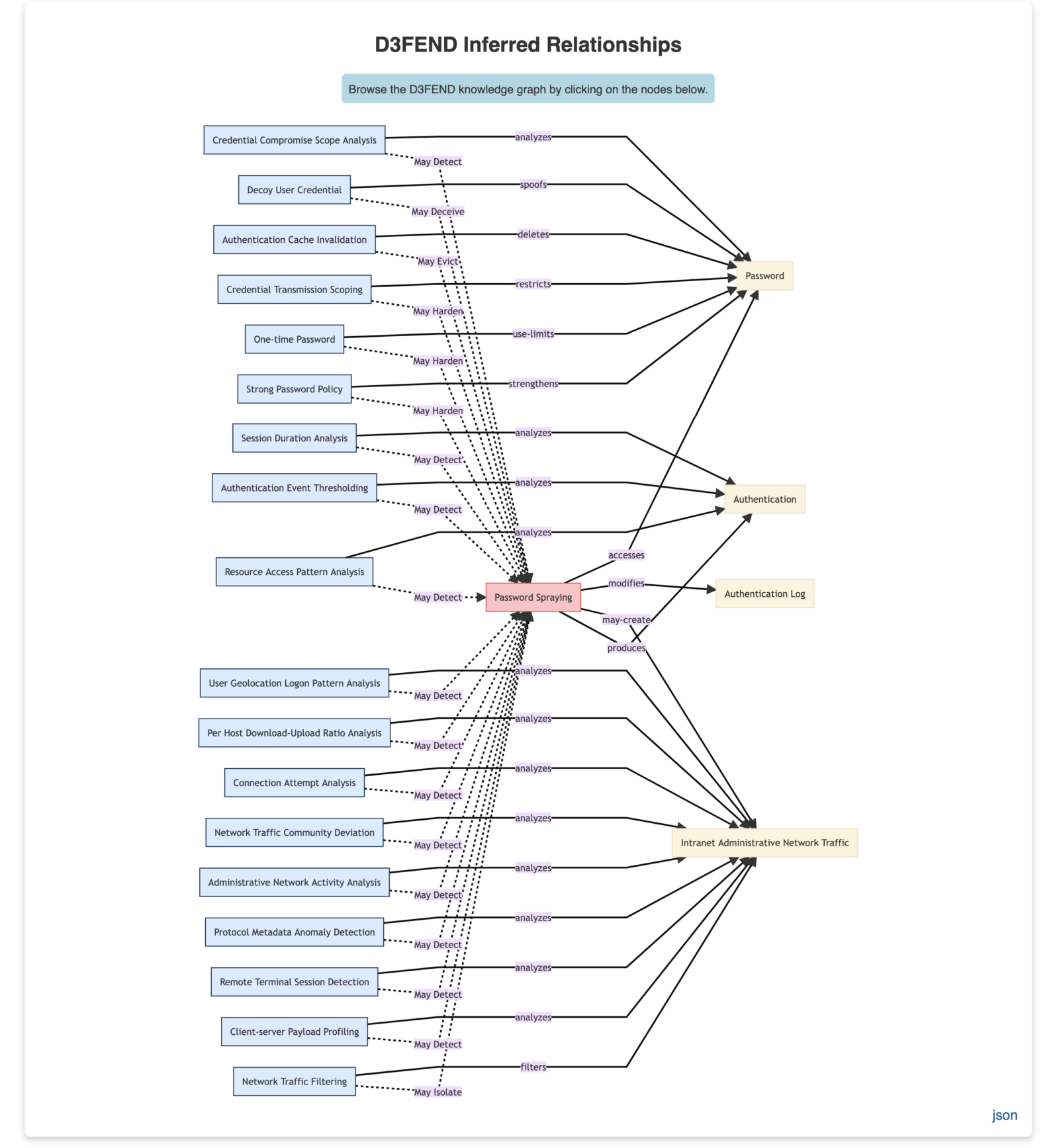
You can dig into each one of the defensive techniques to learn more about how the technique works, as well as things to consider that may impact efficacy:
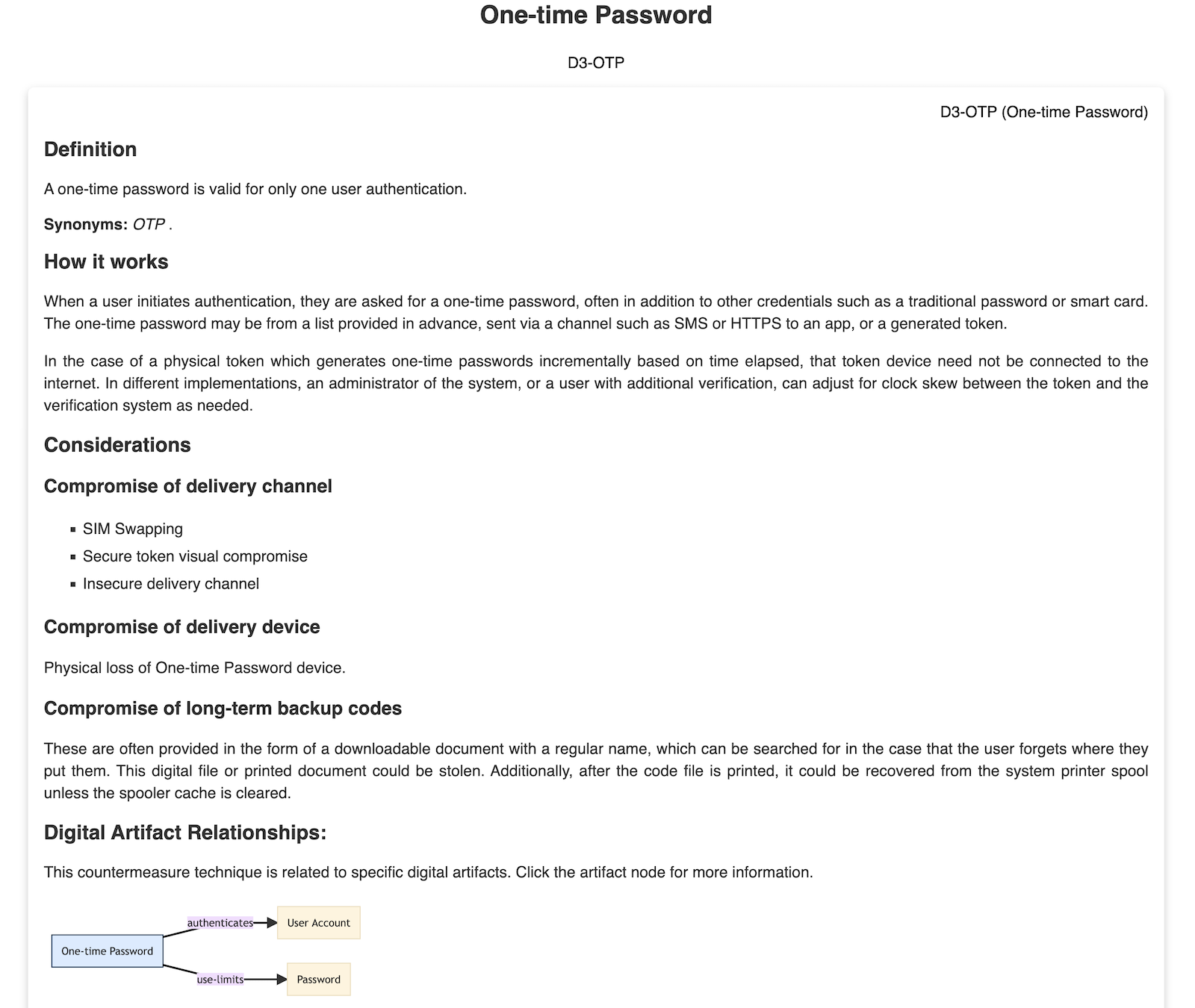
The final section of the detailed view of each defensive technique includes the full inventory of ATT&CK mappings. This is great, especially for visualization in the ATT&CK Navigator so that you can analyze each proposed defensive control against your larger threat model and identify which controls will have the greatest coverage. In this example, we can see that implementation of One-time Passwords (OTP) can not only help harden our environment to prevent a successful password spray attack, but this can also help mitigate the risks of several privilege escalation and persistence techniques that rely on similar attacks meant to discover valid user credentials.
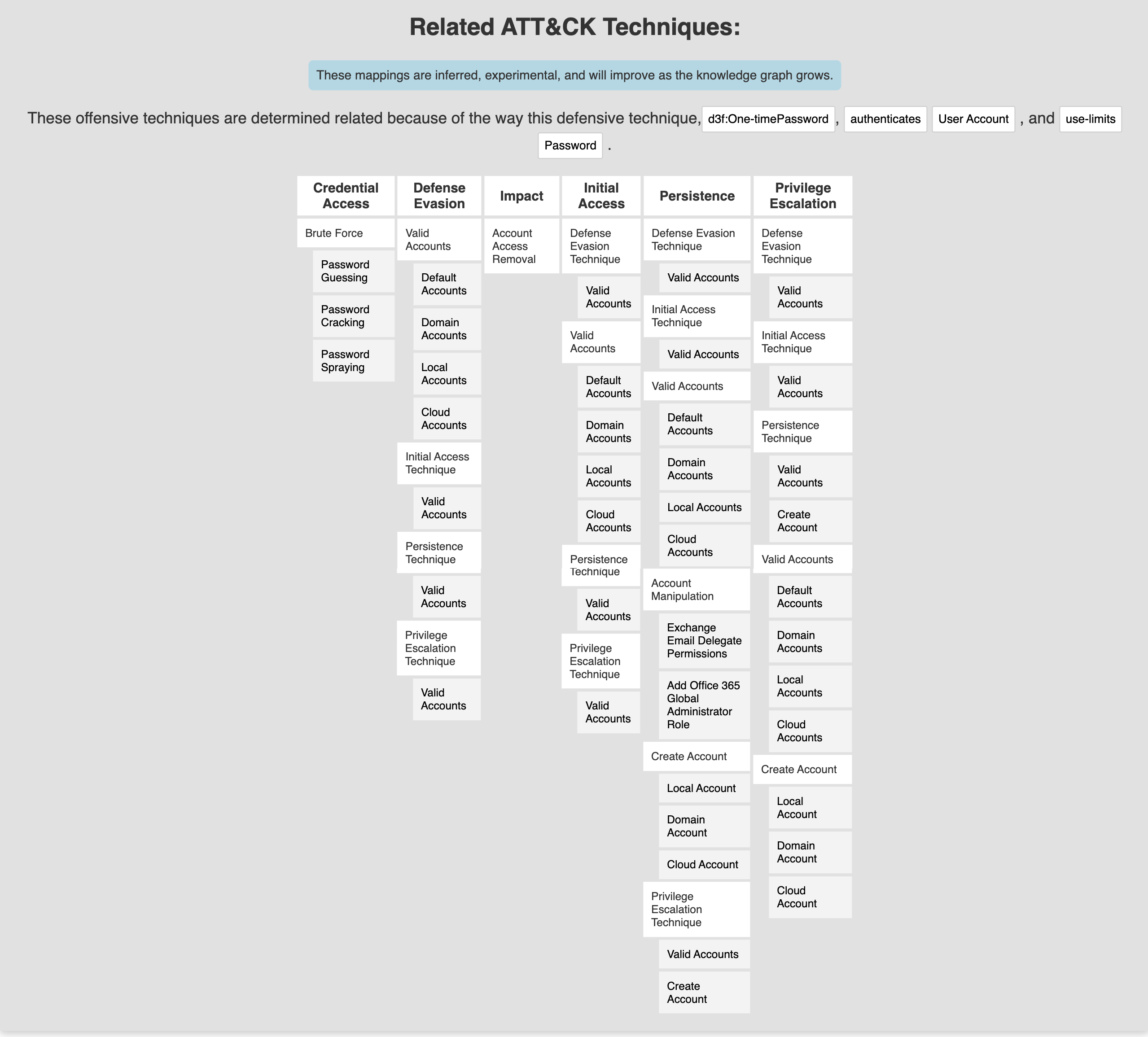
By taking the time to review the defensive controls mapped to any of your target ATT&CK techniques from an emulation exercise, you can start to identify controls that will help build the layers of defense holistically. The goal is to identify the controls that cover multiple attacker techniques. To say it another way, each attacker technique should be facing multiple defensive points, designed to prevent or detect the attacker techniques. Each layer adds complexity to the attacker’s side of the equation, and gives us defenders a chance to respond faster.



